Hash function
Currently the code uses for the packet hash function a double round of SHA-256 (SHA-2). It uses DoubleHashB from "github.com/btcsuite/btcd/chaincfg/chainhash".
It hashes the packet before signing and verifying the signature. The double hash is used to prevent against length extension attacks. There are a couple of alternatives to consider:
- SHA-3 is robust against length attacks (according to google search). While SHA-3 is slower than SHA-2, it should be faster than a double round of SHA-2.
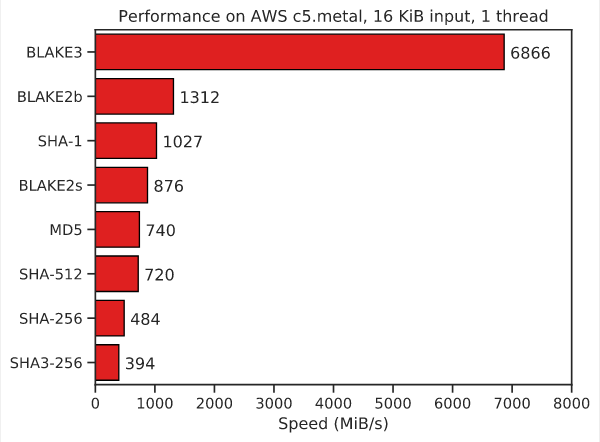
- Blake2 (https://www.blake2.net/) outperforms SHA-3 according to their website. A presentation is here https://www.blake2.net/acns/slides.html
- Blake3 (https://github.com/BLAKE3-team/BLAKE3) outperforms blake2. It started in 2019? and might be too recent to consider.
The downside of blake3 would be missing peer review (pun intended) and missing library support. Some blake3 implementations are barely a year old. Nevertheless it could still make sense. By the time Peernet hits the market there should be more literature and code on blake3 available.
Comments
-
I think the decision is between SHA-3, Keccak-256 (modified sha-3 used by ethereum) or sha-2. SHA-2 has been around longer and is much more battle tested, albeit eventually will be replaced with sha-3 once compromised. SHA-3 is faster in dedicated hardware i.e ASICS, FPMG, etc.
There are other derivatives like kangaroo12 but I like playing it safe and going with something widely used.
Blake3 is way too new to trust. Could be wrong with this but Blake2 seems based on sha-2 so doesn't provide any security benefits if sha-2 is broken. Also online I find a ton of support and validation for the security of Keccak but Blake typically only highlights speed and that worries me.
-
Update for anyone who is interested. Blake3 works great and will be used moving forward. It actually can be considered not that new since it "is based on an optimized instance of the established hash function BLAKE2 and on the original Bao tree mode".
Howdy, Stranger!